Télécharger invisible-ink - [i-i] sur PC
- Catégorie: Business
- Version actuelle: 1.0.7
- Dernière mise à jour: 2021-07-21
- Taille du fichier: 37.68 MB
- Développeur: The Whisper Company
- Compatibility: Requis Windows 11, Windows 10, Windows 8 et Windows 7
Télécharger l'APK compatible pour PC
| Télécharger pour Android | Développeur | Rating | Score | Version actuelle | Classement des adultes |
|---|---|---|---|---|---|
| ↓ Télécharger pour Android | The Whisper Company | 0 | 0 | 1.0.7 | 17+ |







| SN | App | Télécharger | Rating | Développeur |
|---|---|---|---|---|
| 1. |  invisible ink invisible ink
|
Télécharger | /5 0 Commentaires |
En 4 étapes, je vais vous montrer comment télécharger et installer invisible-ink - [i-i] sur votre ordinateur :
Un émulateur imite/émule un appareil Android sur votre PC Windows, ce qui facilite l'installation d'applications Android sur votre ordinateur. Pour commencer, vous pouvez choisir l'un des émulateurs populaires ci-dessous:
Windowsapp.fr recommande Bluestacks - un émulateur très populaire avec des tutoriels d'aide en ligneSi Bluestacks.exe ou Nox.exe a été téléchargé avec succès, accédez au dossier "Téléchargements" sur votre ordinateur ou n'importe où l'ordinateur stocke les fichiers téléchargés.
Lorsque l'émulateur est installé, ouvrez l'application et saisissez invisible-ink - [i-i] dans la barre de recherche ; puis appuyez sur rechercher. Vous verrez facilement l'application que vous venez de rechercher. Clique dessus. Il affichera invisible-ink - [i-i] dans votre logiciel émulateur. Appuyez sur le bouton "installer" et l'application commencera à s'installer.
invisible-ink - [i-i] Sur iTunes
| Télécharger | Développeur | Rating | Score | Version actuelle | Classement des adultes |
|---|---|---|---|---|---|
| Gratuit Sur iTunes | The Whisper Company | 0 | 0 | 1.0.7 | 17+ |
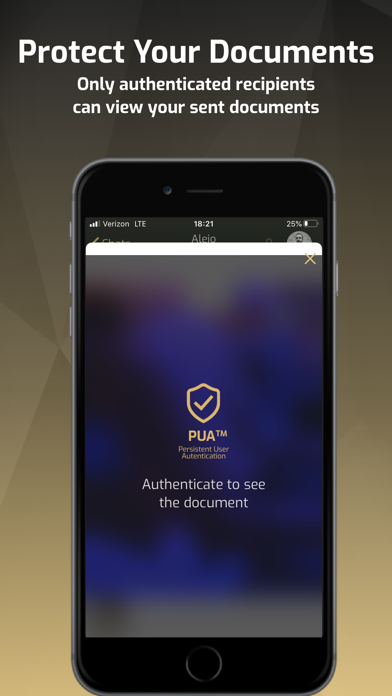
Private documents, messages, and images shared on invisible-ink, or [i-i] for short, are not visible to any unauthorized users. - Powered by patent-pending PUA (Persistent User Authentication), [i-i] authenticates (persistently) the face in front of the screen and only shows the contents in real-time when it sees your eyes. Discuss confidential matters and share private documents with recipients around the world with the confidence that your communication is safe, secure, private, and only accessed by those that are authenticated. - We don’t store your messages unless you want us to: In our [i-i] Servers or in your iCloud (the messages go from your phone to your iCloud.) They remain encrypted. Invisible-ink eliminates unauthorized access to your communications, ensuring that ONLY YOU can view and send your messages. - If a second face appears over your shoulder when you are viewing in private, the screen will obfuscate. Our encryption only decrypts real-time when the authenticated face is looking at the screen. If the authenticated face leaves the screen or another face appears, the contents on the screen disappear. - When a document is received you have the certainty and peace of mind that the document could only have been sent by one (authenticated) person, and conversely, when you send a document, you know only one person can view it. - [i-i] allows you to communicate digitally with the same privacy and security as having a face-to-face conversation. Invisible-ink protects your business, employees, clients, intellectual property, and your reputation from spying eyes and hackers. - When sending documents, images, or videos you decide if the recipient can export or save what you send. - Secure your business documents and clients’ private information. The way you are the owner of the phone, you should be the owner of your messages. - Choose how long a message is visible to recipients in the conversation, from 1 second to 1 week. - You can change the number of faces allowed, how often the PUA authentication is triggered, and how long your eyes can be off-screen before blocking the screens’ content. Communications stay invisible to unauthorized users. Maintain ownership of what you send, even after it leaves your phone. - We believe in “ownership” and believe you are the owner of your data and communications. - You can delete your messages for you and for everyone in the conversation at any point. - Your communication is safe with military-grade end-to-end AES-256 encryption. We call the digital version of face-to-face “eye-to-eye” or [i-i]. - Your messages just like your phone are yours. - Our application maintains your communication encrypted when it arrives on your device. - Keys are generated locally and stay locally in the device. - We give you the ability to share or not share your metadata with your recipients. They are locally stored on your device and never stored in our servers. - We don’t have your encryption keys. - Once the message is opened, the timer starts and deletes once it goes off. You are the only person that can see your communications. - We do not save or backup your data unless you opt-in.